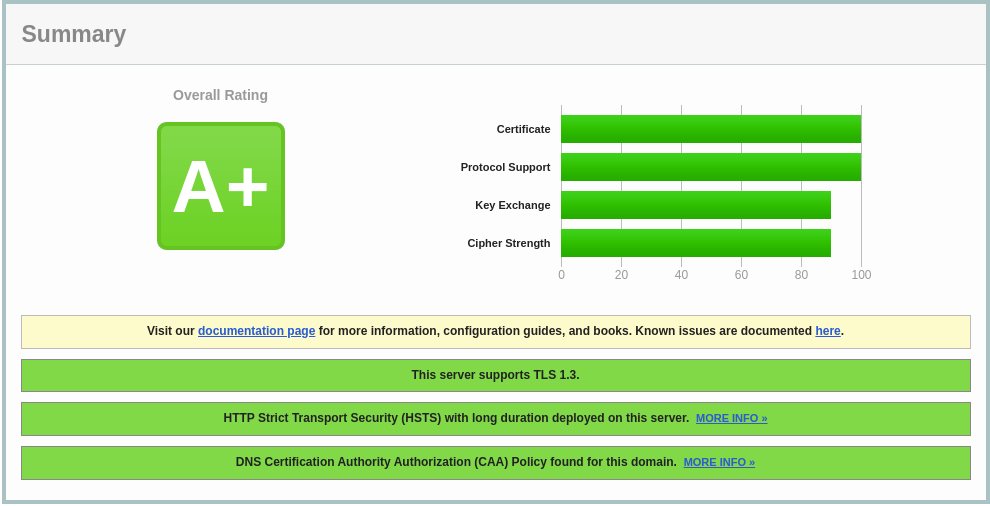
Yesterday I scanned this site using the following tools:
- SSL Labs: SSL Server Test: TLS version, cipher suites, and security headers scanner.
- Security Headers: HTTP response security headers scanner.
- Lighthouse: Page performance and accessibility scanner.
I made a several Apache configuration changes based on the initial scan results:
- Disabled ancient versions of TLS.
- Set an explicit cipher suite list using the Mozilla SSL Configuration Generator.
- Refined the value of the
Access-Control-Allow-Originheader. - Added two new headers:
Referrer-PolicyandPermissions-Policy.
After a couple of iterations of changes and testing, I:
- Updated my recent post to reflect the response header changes in the Apache configuration.
- Applied the same changes (with minor tweaks) to several other sites.
Tip: Use the Mozilla SSL Configuration Generator to generate your TLS configuration. It has three client profiles (“modern”, “intermediate”, and “old”) and supports a variety of servers (web, email, database, application, etc).
Random thoughts:
- Static site generators like Hugo and Jekyll make it easy to check off many performance and security requirements.
- As an industry, we still have not learned to “have one joint and keep it well oiled” when dealing with security. Notable exception: Wireguard.
Screenshots of the improved scan results are available below. Click the SSL Labs and Security Headers pictures to see the scan details.
Security Headers scan results.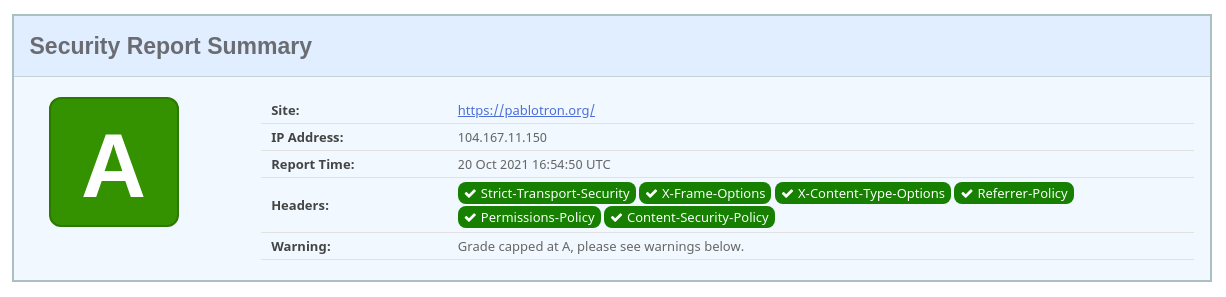
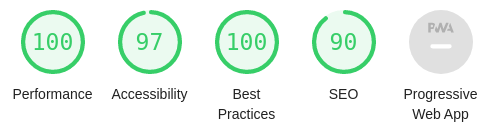
Lighthouse desktop scan results.